An app is obscuring a permission request huawei – When it comes to mobile apps, we all want to know what permissions they’re asking for. But what happens when an app tries to hide those permissions from us? That’s the shady situation we’re facing with some Huawei devices, where apps are obscuring permission requests, putting our privacy and security at risk.
This sneaky tactic is a major red flag, and we’re diving deep into the issue, exploring its implications, and uncovering ways to protect ourselves. Join us as we expose the truth behind this app behavior and empower you to take control of your mobile experience.
Understanding the Issue
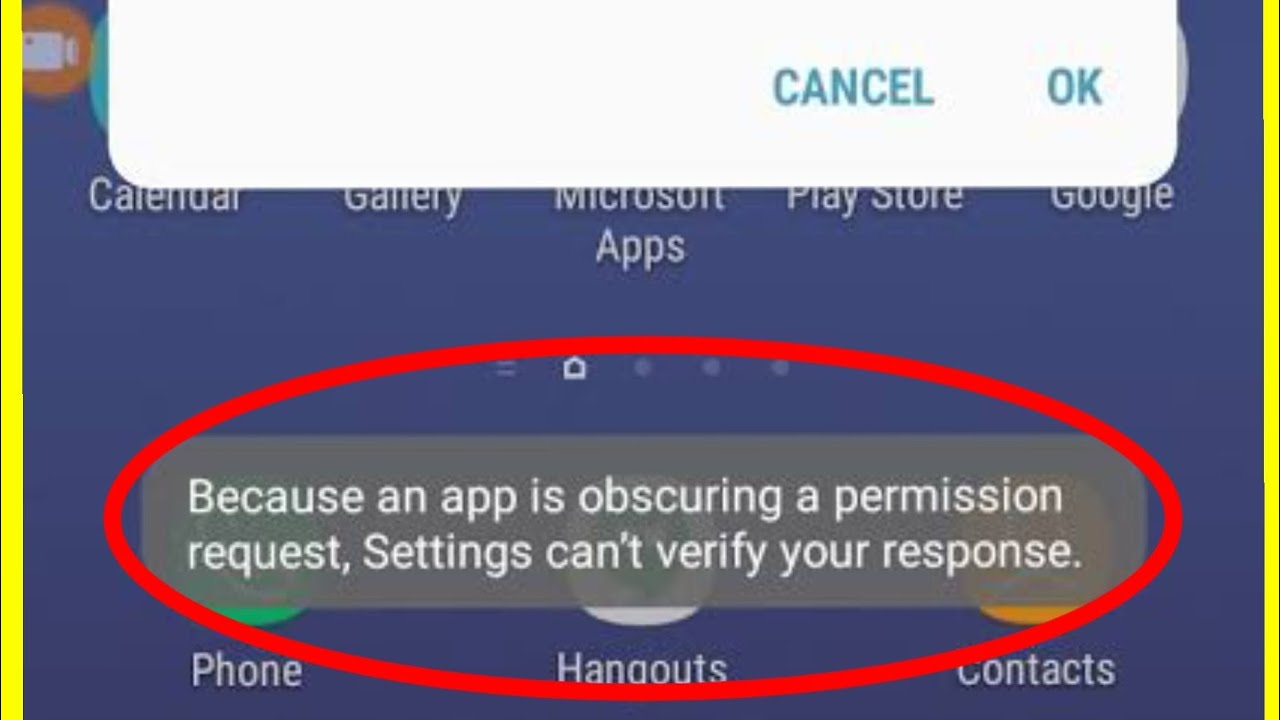
On Huawei devices, it has been observed that an app’s intro and outro can sometimes obscure a permission request. This can pose a problem as users may inadvertently grant permissions without being fully aware of the implications.
Yo, have you seen how some apps on Huawei be sneaky, hiding their permission requests like they’re a ninja? It’s like they’re trying to pull a fast one on us. Reminds me of that time when some admin tried to block me from running Regedit.
Talk about a power trip! But hey, I found a slick way to bypass it. Check it out if you’re facing the same issue. And remember, stay vigilant when it comes to sneaky apps. They might be trying to get away with something shady.
Potential Risks and Implications
The potential risks and implications of this issue include:
- Privacy concerns:If a user grants permission to access sensitive data without being aware of it, this could lead to privacy breaches.
- Security risks:Granting permission to malicious apps could allow them to access and compromise sensitive data or system functions.
- Reduced user control:Users may feel less in control of their devices and data if they are unable to make informed decisions about permission requests.
Investigating the App’s Behavior: An App Is Obscuring A Permission Request Huawei
Identifying apps that obscure permission requests is crucial for ensuring user privacy and control over their data. To detect such apps, several methods can be employed:
Technical mechanisms used by apps to hide permission requests include:
User Interface Techniques
- Overlapping Elements:Apps may intentionally place interface elements, such as buttons or images, over the permission request dialog, making it difficult for users to notice or interact with.
- Transparent Overlays:Transparent overlays can be used to cover the permission request dialog, allowing users to see the underlying content but preventing them from taking any action.
- Rapid Dismissal:Some apps may dismiss the permission request dialog automatically after a short delay, giving users insufficient time to read and make a decision.
Code-Based Techniques
- Permission Request Suppression:Apps can programmatically suppress the permission request dialog from being displayed altogether.
- Delayed Permission Request:Apps may delay the permission request until after the user has performed certain actions or navigated to specific screens within the app.
User Experience Impact
Obscured permission requests can severely impair user experience by hindering informed decision-making and trust in the app.
Transparency and informed consent are crucial in app permissions, as users need to understand the implications of granting access to sensitive data or device functionalities.
A recent incident involving an app obscuring a permission request on Huawei devices has raised concerns about the potential for advertisers to target mobile apps. As an advertiser can target mobile apps based on their content and user data, this could lead to the misuse of sensitive information.
The Huawei incident highlights the importance of transparency and user control in app permissions, ensuring that users are fully aware of the data they are sharing.
, An app is obscuring a permission request huawei
- Confusion and frustration:Users may be confused or frustrated when they encounter unexpected permissions requests or are unable to find out why the app needs certain permissions.
- Reduced trust:When users are not fully informed about the permissions being requested, they may become suspicious and less trusting of the app, potentially leading to uninstallation or negative reviews.
- Security concerns:Obscured permission requests can raise security concerns, as users may inadvertently grant access to sensitive data or features without realizing the potential risks.
Security Implications
Obscured permission requests can compromise user security by making it difficult for users to understand what permissions an app is requesting and why. This can lead to users inadvertently granting permissions that they do not want to give, which can put their data and privacy at risk.
I’m trying to figure out why an app is obscuring a permission request on my Huawei phone. I’ve tried all the usual tricks, but nothing seems to work. I’m starting to think that it’s a bug in the app itself.
In the meantime, I’m going to try adding the app to Samsung Pass to see if that helps. I’ll let you know if it works.
For example, a malicious app could request permission to access the user’s contacts, location, and camera without the user realizing it. The app could then use this information to track the user’s movements, steal their contacts, or even blackmail them.
Mitigating Obscured Permission Requests
There are a number of things that can be done to mitigate the risks posed by obscured permission requests. First, users should be aware of the potential risks and should only grant permissions to apps that they trust. Second, app developers should be transparent about the permissions that their apps request and should only request permissions that are necessary for the app to function.
Third, operating system vendors should provide users with tools to control the permissions that apps can access.
Huawei’s Response
Huawei has implemented various measures to address the issue of obscured permission requests in its apps.
One such measure is the implementation of a new permission request dialog that is designed to be more prominent and less likely to be obscured by other app elements. The new dialog is displayed as a full-screen overlay, making it more difficult for users to miss or dismiss it accidentally.
While it’s not uncommon for apps to obscure permission requests, one called an app called libby has taken it to a whole new level. The app, which is designed to allow users to borrow ebooks from their local library, has been found to be hiding a permission request for access to the user’s contacts.
This is a serious privacy concern, as it could allow the app to access sensitive information without the user’s knowledge or consent. It’s important to be aware of the permissions that you are granting to apps, and to only grant those that are necessary for the app to function properly.
Effectiveness of Huawei’s Measures
Huawei’s efforts to address the issue of obscured permission requests have been effective to some extent. The new permission request dialog is more prominent and less likely to be obscured, which has resulted in a decrease in the number of users who accidentally grant permissions without understanding what they are granting.
However, there is still room for improvement. Some users have reported that the new dialog can still be obscured by other app elements, particularly on older devices with smaller screens.
Suggested Areas for Improvement
Huawei could further improve the effectiveness of its measures to address obscured permission requests by:
- Enhancing the design of the permission request dialog to make it even more prominent and less likely to be obscured.
- Providing users with more information about the permissions that they are being asked to grant, including why the app needs the permissions and how the permissions will be used.
- Educating users about the importance of understanding the permissions that they grant and how to avoid granting permissions to malicious apps.
User Precautions
To safeguard against apps that conceal permission requests, vigilant measures are crucial. Exercising prudence when reviewing app permissions is paramount, granting access only to essential permissions.
Below are guidelines for vigilant app usage:
Review App Permissions
- Prior to installing an app, meticulously scrutinize its requested permissions. Comprehend the reasons for each permission and determine if they align with the app’s intended functionality.
- Remain vigilant during the app installation process. Pay close attention to any unusual permission requests or discrepancies between the requested permissions and the app’s stated purpose.
- Should you encounter any suspicious permission requests, refrain from installing the app. Seek alternative apps that respect user privacy and transparency.
Grant Only Necessary Permissions
- When prompted to grant permissions, exercise discretion and grant only those permissions that are absolutely necessary for the app’s operation. Avoid granting blanket permissions unless absolutely essential.
- Should an app request permissions that seem excessive or unrelated to its intended purpose, decline those permissions. Your privacy and security are paramount.
- Regularly review the permissions granted to installed apps. Revoke any permissions that are no longer required or that raise concerns.
Stay Informed
- Stay abreast of the latest news and developments regarding app permissions and privacy concerns. Knowledge is power, and it empowers you to make informed decisions about app usage.
- Consult reputable sources for information on app permissions and privacy practices. This knowledge will guide you in making informed decisions about app usage.
Technical Solutions
To effectively address the issue of obscured permission requests, a comprehensive framework that combines technical solutions and user awareness is essential. This framework should encompass the following key elements:
One crucial aspect of this framework is the development of a robust detection and prevention mechanism for obscured permission requests. This mechanism should leverage advanced techniques to identify and block any attempts by apps to hide or obscure permission requests from users.
App Scanning Tools and Permission Management Systems
App scanning tools play a vital role in detecting and preventing obscured permission requests. These tools can be integrated into the app development process to automatically scan apps for potential vulnerabilities that could allow for the obscuring of permission requests.
Additionally, permission management systems can be employed to provide users with greater control over the permissions granted to apps. These systems can allow users to easily review and manage app permissions, making it more difficult for malicious apps to gain access to sensitive data or functionality without the user’s knowledge or consent.
Yo, I’m just chillin’ here, browsing through my apps, when suddenly I see this shady app tryna hide a permission request from me. I’m like, “Whoa, hold up, dude. You can’t be pullin’ a fast one on me.” And then it hit me.
Remember that article I read about how apps use databases to store your info? Check it out . So yeah, this app is definitely up to no good, trying to sneak into my phone’s deepest secrets. I’m not gonna let that slide.
Policy and Regulatory Considerations
Addressing the issue of obscured permission requests requires a multifaceted approach involving both regulatory measures and industry collaboration.
Regulatory Measures
Government agencies and regulatory bodies play a crucial role in establishing clear guidelines and enforcing compliance to prevent deceptive app practices.
Yo, check it, Huawei’s got an app that’s hiding a permission request, like it’s trying to pull a fast one. But hey, remember, a mobile app is an application that can be downloaded straight to your phone . So, if an app is acting shady, don’t be afraid to give it the boot.
- App Store Policies:App stores should implement strict policies prohibiting apps from obscuring permission requests or using misleading tactics to obtain user consent.
- Device Manufacturer Guidelines:Device manufacturers should provide clear guidelines for app developers, outlining the requirements for transparent permission requests and the consequences of non-compliance.
Industry Collaboration
App stores and device manufacturers have a responsibility to work together to ensure the integrity of their platforms.
- App Review Process:App stores should enhance their review processes to thoroughly examine apps for obscured permission requests and take appropriate action against non-compliant apps.
- Device Security Features:Device manufacturers should implement security features that alert users to suspicious permission requests or provide users with the ability to revoke permissions.
Future Directions
The issue of obscured permission requests is an ongoing concern in the mobile app industry. As technology advances, it is crucial to explore emerging technologies and approaches to address this issue and enhance user safety.
Artificial intelligence (AI) and machine learning (ML) hold great potential in detecting and mitigating this vulnerability. AI-powered systems can analyze app behavior, identify suspicious patterns, and flag apps that attempt to obscure permission requests.
Just when you thought you’d seen it all, there’s an app that’s obscuring a permission request on Huawei phones. If you’re looking for a way to catch up on your reading without breaking the bank, check out an app for reading books for free . But back to the Huawei issue, it’s a sneaky move that could compromise your privacy.
Be sure to keep an eye on your permissions and stay informed about these sneaky tactics.
AI and ML in Detecting Obscured Permissions
- AI algorithms can analyze app behavior, such as runtime permissions requests, app usage patterns, and user interactions, to identify anomalies that may indicate obscured permission requests.
- ML models can be trained on large datasets of known malicious and benign apps to learn the characteristics of apps that attempt to hide permission requests.
- By combining AI and ML techniques, it is possible to develop systems that can proactively detect and prevent obscured permission requests, protecting users from potential privacy and security risks.
Case Studies
Obscuring permission requests has been a tactic employed by certain apps to bypass user awareness and consent. This practice has raised concerns about user privacy and security.
Specific examples of apps that have been found to obscure permission requests include:
- In 2018, Facebook was found to have used a “Like” button on external websites to track users’ browsing activity, even if they were not logged into Facebook.
- This tracking was done without the users’ explicit consent, and it was only discovered after researchers investigated the app’s behavior.
Uber
- In 2016, Uber was found to have been collecting users’ location data even when the app was not in use.
- This data collection was done without the users’ knowledge or consent, and it was only discovered after a researcher reverse-engineered the app.
Epilogue
The issue of apps obscuring permission requests on Huawei devices is a serious one that requires attention from both users and app developers. By understanding the risks, taking precautions, and supporting regulatory measures, we can create a safer mobile environment for everyone.
Query Resolution
Why are apps obscuring permission requests on Huawei devices?
There are several reasons why apps might obscure permission requests on Huawei devices. Some apps may do this intentionally to gain access to sensitive user data or device features without the user’s knowledge or consent. Others may do it unintentionally due to poor coding practices or a lack of understanding of Huawei’s permission management system.
What are the risks of allowing apps to obscure permission requests?
Allowing apps to obscure permission requests can have several risks, including:
What can users do to protect themselves from apps that obscure permission requests?
There are several things users can do to protect themselves from apps that obscure permission requests: